Information Security and Cryptography | Final Term Past Paper | Superior University | VU Exam Guide
Table of Contents
Unlocking the Secrets of Digital Safety: Dive into Information Security and Cryptography
It is impossible to overestimate the significance of protecting sensitive data in the current digital era, when data breaches and cyberattacks are becoming more frequent. This is where information security and cryptography, a crucial area of cybersecurity, come into play. Exam problems and subjects related to information security and cryptography can be better understood by looking at previous information security and cryptography papers if you’re getting ready for your last term at Superior University. Vuexamguide.com is a comprehensive collection of these old papers and is an invaluable tool for students who want to do well on their exams.
Introduction to Information Security and Cryptography
Within computer science, information security and cryptography is a specialized field that focuses on data protection via encryption and other security methods. It deals with creating and putting into place safe systems that guard against unwanted access and guarantee the confidentiality and integrity of data.
Learning Outcomes
After completing a course in Information Security and Cryptography, students will have a deep understanding of:
- Encryption and decryption techniques
- Network security protocols
- Cryptographic algorithms (such as RSA, AES, and SHA)
- Digital signatures and certificates
- Security practices for protecting against threats like malware, phishing, and hacking.
Importance of the Subject
Various applications rely heavily on Information Security and Cryptography:
- Banking and Finance: Secure transactions and communications between banks and their clients.
- E-Commerce: Encryption of customer data and financial information during online purchases.
- Healthcare: Protection of patient records and confidentiality of medical information.
- Government: Securing classified information and safeguarding national security.
Historical Context
Although cryptography has been used since antiquity, the modern application of information security gained prominence during World War II because to devices like the Enigma that were used to encrypt and decode military communications. This was the first instance of what is now known as modern cryptography.
Career Opportunities and Salary Expectations
Graduates in Information Security and Cryptography have diverse career opportunities, including roles as:
- Information Security Analysts
- Cryptographers
- Security Software Developers
- Compliance and Security Officers
According to industry reports, the average salary for information security roles ranges from $70,000 to $120,000, varying by experience, location, and specific job role.
Achievements and Benefits
By mastering Information Security and Cryptography, students can:
- Play a critical role in building a safer digital world.
- Gain skills that are in high demand across multiple industries.
- Contribute to innovations in the field of digital security.
Market and Future Value
The requirement for regulatory compliance and the rise in cyber threats worldwide have led to a notable increase in the market value of information security and cryptography. With developments in artificial intelligence and quantum computing opening up new avenues for security and encryption techniques, the future appears even more promising.
Exam Insights
Understanding the foundational ideas and practical applications of cryptography and information security is essential for test success. Examine Superior University past papers (available at vuexamguide.com), as these focus on real-world scenarios and security-related problem-solving, and can help students prepare for the kinds of problems that might be presented.
FAQs about Information Security and Cryptography
Q1: What is the difference between encryption and decryption?
A1: Encryption is the process of converting plain text into cipher text to secure it, while decryption is the reverse process, converting cipher text back to plain text.
Q2: Can cryptography be broken?
A2: While many cryptographic algorithms are considered secure, none are completely unbreakable. It depends on the algorithm’s strength and the computational power available.
Q3: What is a cryptographic hash function?
A3: It is a function that converts an input (or ‘message’) into a fixed-size string of bytes. The output is typically a ‘hash code’ or ‘digest’ that is unique to each unique input.
Interview Questions to Expect
- Explain the difference between symmetric and asymmetric encryption.
- What are the potential vulnerabilities of a cryptographic system?
- How does a digital signature work and what are its uses?
Information Security and Cryptography Final Term Past Paper
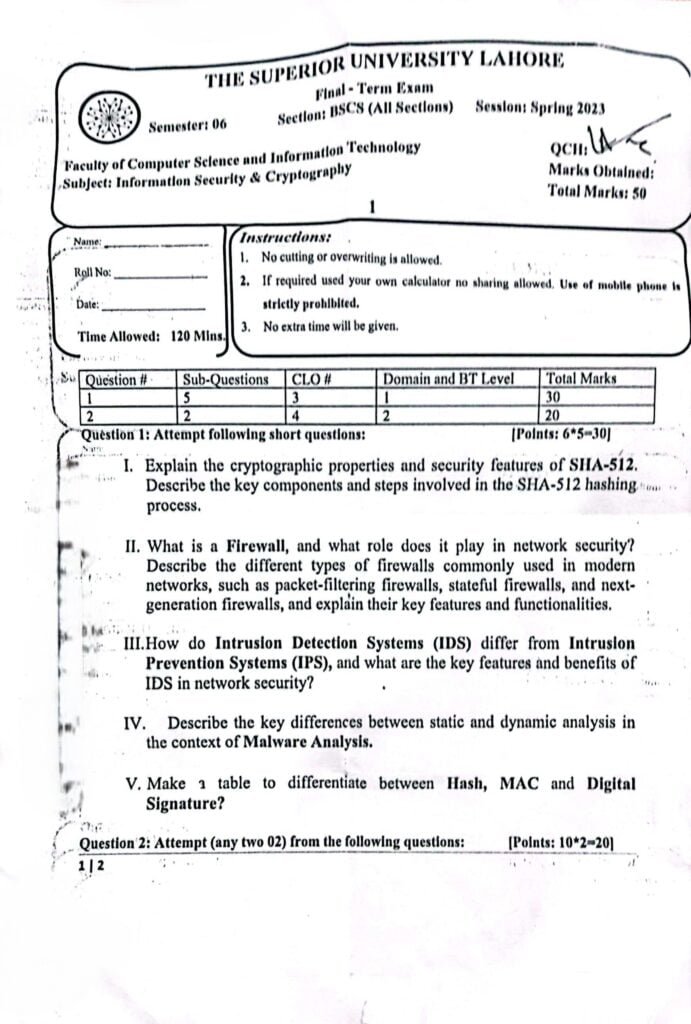

Note: You can also checkout all Subject Final Term Past Papers of Superior University.
Conclusion
In the modern world, information security and cryptography are not merely topics; they are essential to digital trust and security. Through the use of sample tests, like those from Superior University that are accessible at vuexamguide.com, students can enhance their exam preparation and position themselves for success in a career that protects digital environments.
Visit vuexamguide.com for more resources and exam-ace strategies. There, you may obtain all the practice tests and past papers need to guarantee your success.
 Virtual University
Virtual University
 Superior university
Superior university